This shift is characterized by the increased interconnectivity of systems, smart automation, and the use of digital technologies such as the Internet of Things (IoT) and artificial intelligence (AI) to improve the efficiency and productivity of businesses.
The water sector is no exception to this trend, and is already seeing the adoption of digital solutions to manage water supply and treatment. Digitalisation has the potential to improve the efficiency and effectiveness of water management, but it is crucial that security measures are put in place to protect against cyber threats and other potential vulnerabilities. Indeed, with the increased use of technology comes new security risks, and it is important for the industry to transition into this Industry 4.0 in a secure and responsible manner.
Digital solutions for the water sector
Started in 2019 and finished in November 2022, the digital-water.city (DWC) project developed and demonstrated 15 advanced digital solutions for the water sector. These solutions cover the whole range of innovative digital technologies, such as augmented reality, mobile technology, cloud computing, sensors, real-time monitoring, artificial intelligence, predictive analytics, modelling, and open-source software. The project is active in five European urban and peri-urban areas and services 30 million European citizens. SINTEF was involved in both the development of digital solutions and to ensure their security. In particular, we strived to provide practical security recommendations to digital solutions’ owners and water utilities and to help raising security awareness within engineering teams by shedding light on the most common issues that comes with the integration of digital solutions.
“What is a digital solution in practice?”, you might ask. It turns out digital solutions can be quite different from one another. Their common point is that they usually make use of some digital technologies to help operators of a water utilities to take better decisions (such as when to perform maintenance). To better understand the potential security risks, we classified the digital solutions in three subsets, depending on their level of integration with the water utilities:
- Standalone solutions: These are solutions which are not interacting with any sensors or utilities. They can be Web or Mobile Applications, publicly available or requiring authentication.
- Solution with “external” sensors: These are the solutions that are gathering data from sensors “in the wild”, using some long-range wireless technology (mobile networks, LoRa or Sigfox for instance) or manually gathered using most likely shorter-range wireless protocols, such as Bluetooth (Low Energy).
- Solution with “internal” sensors: These are the solutions that are gathering data from sensors that are placed in the water utilities (but not necessarily connected to their systems).
From there, we defined a generic architecture for a digital solution in the DWC project. We believe, however, that this architecture applies to most digital solutions, independently from the domain. Figure 1 presents this architecture.
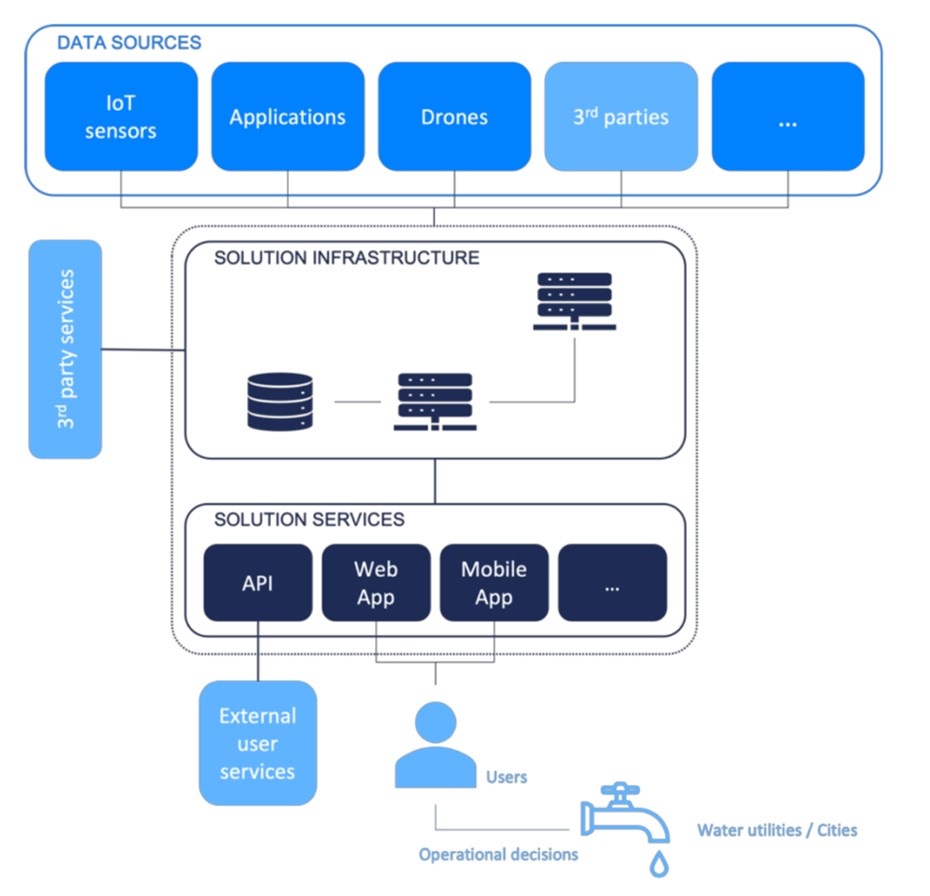
- Data sources: Digital solutions use external data, which is analyzed and transformed to provide added value. This data can come from various sources such as IoT sensors, 3rd party services, and drones. The applications developed by a solution can also be considered as a data source.
- Solution infrastructure: Most solutions use a backend infrastructure to operate their service. This can include on-premises servers, cloud servers, and 3rd party services used for data collection.
- 3rd party services: These are services used by a solution to provide their own service, such as SMS or email sending capabilities.
- Solution’s services: Solutions provide a service to water utilities/users, such as an alert if the level of E. Coli bacteria is too high in a water basin. A service can be exposed to users in various forms, such as a web or mobile application or API.
- Users of the solution’s services:
- Regular users: Users of the service are operators in a water utility who need to make operational decisions based on the information provided by the digital solution’s service.
- Machines: If the service is exposed via an API, it may be used by another solution or directly by a water utility to integrate it into their own system.
Attacks against digital solutions
Digital solutions can be complex and might interact with several external actors to collect data, access services or to simply provide their own service to their users. Attackers thus get a wide choice of attack vectors when targeting a digital solution: IoT devices, applications, 3rd party services, etc. Figure 2 presents the different classes of attack identified against digital solutions in DWC.
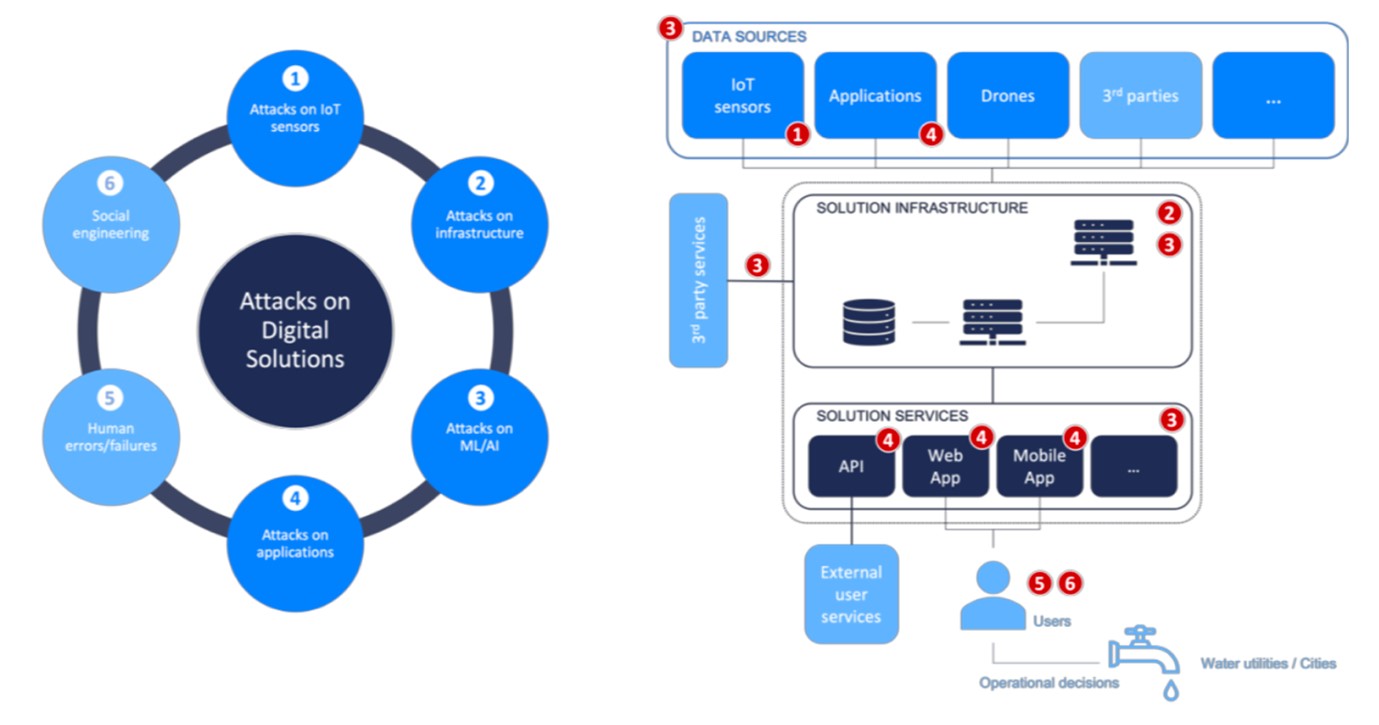
- Attacks on IoT sensors: IoT sensors are a key component for many solutions because they provide the data for these solutions. However, sensors are vulnerable because they are often accessible and difficult to secure. An attacker may manipulate sensor data to trigger incorrect outputs by services, which could have severe consequences. In addition, IoT sensors have been compromised at scale and used in botnets.
- Attacks on infrastructure: Attacking the infrastructure is a way for attackers to disrupt services or gain unauthorized access to resources. This could also be used to later attack a water utility using the compromised service.
- Attacks on ML/AI: Attacks against Machine Learning (ML) and Artificial Intelligence (AI) are less well-known, but attackers can use crafted inputs to mislead algorithms. Models also have an intrinsic value, and attackers may want to steal them.
- Attacks on applications: Applications (Web, Mobile, API, etc.) are often exposed, and if compromised can lead to data leaks, unauthorized access, and data manipulation.
- Human errors/failures: Human error can lead to the same consequences as an attack. If a user is given access to data or actions they should not have, they may misuse it, effectively creating a situation similar to an attack.
- Social engineering: A user may be tricked into performing harmful actions by a malicious person, potentially leading to dangerous consequences.
Digital solutions based on IoT are especially at risk because IoT devices, such as sensors, are often deployed in the wild and are difficult to secure. These devices are typically designed to be easily accessible (cheap), which makes them vulnerable to attacks. In addition, because IoT devices are often connected to the internet, attackers can remotely access and manipulate them.
The risk associated with IoT devices is often overlooked because these devices are relatively new and the technology is still evolving. As a result, many companies and organizations may not have adequate security measures in place to protect against attacks on IoT devices. Additionally, because IoT devices are often considered low-risk, they may not receive the same level of attention and investment in security as other, more sensitive systems. This can make them an attractive target for attackers. Indeed, an attacker could misuse a digital solution based on IoT to compromise a water utility in several ways. For example, an attacker could target the IoT sensors used by the digital solution to collect data. By manipulating the sensor data, the attacker could cause the digital solution to provide incorrect information to the water utility, leading to operational errors or other problems.

Another potential attack would be to target the infrastructure used by the digital solution. By launching a denial-of-service (DoS) attack on the infrastructure, the attacker could disrupt the services provided by the digital solution, making it difficult or impossible for the water utility to access the information it needs to operate effectively. In addition, an attacker could use the digital solution as a way to gain unauthorized access to the water utility’s systems. Once the attacker has gained access, they could manipulate or steal data, or cause other problems for the water utility. Overall, there are many ways that an attacker could misuse a digital solution based on IoT to compromise a water utility, and it is important for water utilities to be aware of these risks and take appropriate steps to protect themselves.
Interconnectivity makes it more challenging to prevent cyber attacks
The traditional approach to protecting critical infrastructure, which involves segmenting networks, is becoming less effective because of the increased interconnectivity of systems. In the past, segmenting networks helped to protect critical infrastructure by limiting access to certain parts of the network and making it more difficult for attackers to move laterally within the network. However, with the rise of IoT and other technologies that enable increased interconnectivity, this approach is no longer sufficient.
One reason for this is that IoT devices, which are often used to collect data for digital solutions, are typically designed to be easily accessible. This means that they are often connected to the internet and can be remotely accessed and manipulated. As a result, even if a network is segmented, an attacker could still potentially gain access to the network through an IoT device. Additionally, the increased use of cloud services and other third-party services makes it more difficult to segment networks and limit access. In many cases, data and services are shared across multiple networks, making it more challenging to control access and protect critical infrastructure.
In particular, we showed that even if a digital solution is not directly connected to a critical infrastructure (such as in DWC), it can still be misused by an attacker to have an operational impact: by exploiting for instance an IoT-based digital solution and manipulating the data, an attacker could trick the AI model into making wrong predictions, which could lead to the operators taking potentially harmful decisions.
Overall, the traditional approach to protecting critical infrastructure by segmenting networks is no longer sufficient in today’s interconnected world. New, more effective approaches are needed to protect against the growing threat of cyber attacks.











Comments
No comments yet. Be the first to comment!